The Analog Gap: The Fundamental Weakness in Digital Credentials
Every digital credential system faces the same challenge - proving the right person is in control
The Problem
Traditional credential systems verify that certificates are valid, devices are authentic, and credentials haven't been revoked. But they cannot prove that the person presenting the credential is actually the legitimate holder.
This vulnerability—what we call "the analog gap"—exists at the intersection of digital security and human verification. A credential can be cryptographically perfect, but if someone else gains access to it, the security model breaks down.
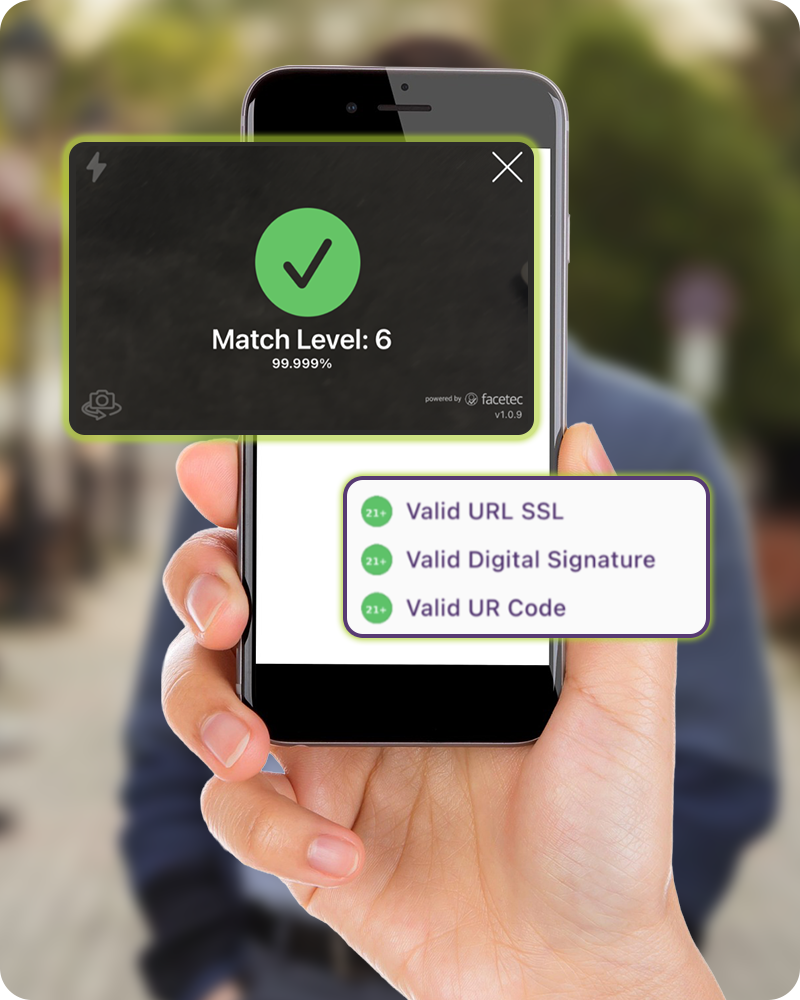
Visualizing the Analog Gap
See how the gap between digital credentials and human verification creates security vulnerabilities
The Cost of Inaction
Fraud Costs
Billions lost annually to credential fraud, identity theft, and verification failures
Liability Risk
Organizations face legal and reputational damage when fraudulent credentials are accepted
Operational Overhead
Help desk calls, manual verification, and fraud remediation consume resources
Real-World Impact

Diploma Frauds
The $1B+ diploma fraud industry thrives because employers cannot easily verify degree authenticity without contacting institutions.

Professional License Fraud
Unlicensed practitioners use stolen or forged credentials, putting public safety at risk.

Identity Theft
Stolen digital credentials enable identity theft and fraud, with victims facing years of recovery.
Why FaceLock Wins
Five core differentiators that set FaceLock apart from traditional credential systems
Offline-First Verification
Complete offline capability - credentials work anywhere, anytime without internet connectivity.
Universal Accessibility
Works with any smartphone camera - no special hardware required for verification.
Zero Data Collection
Privacy-first approach with no accounts or data harvesting during verification.
Cross-Medium Flexibility
Same technology works on digital displays and printed materials.
PKI-Grade Security
Cryptographically signed credentials with biometric binding for maximum security.
iBeta Certified
FaceTec Level 1 & 2 certified 3D liveness detection - highest standards in anti-spoofing.
FaceLock vs Alternatives
See how FaceLock compares to traditional PKI, mobile driver's licenses, and physical ID cards
| Feature | FaceLock | Traditional PKI | Mobile Driver's License | Physical ID Cards |
|---|---|---|---|---|
| Offline Verification | ||||
| Biometric Binding | ||||
| Universal Access | ||||
| Zero Data Collection | ||||
| Cross-Medium Support |
Three Steps: Scan, Face, Trust
Anyone can verify a FaceLock credential in seconds

Scan
Scan the FaceLock UR Code with any smartphone camera

Face
Look at the camera for biometric verification
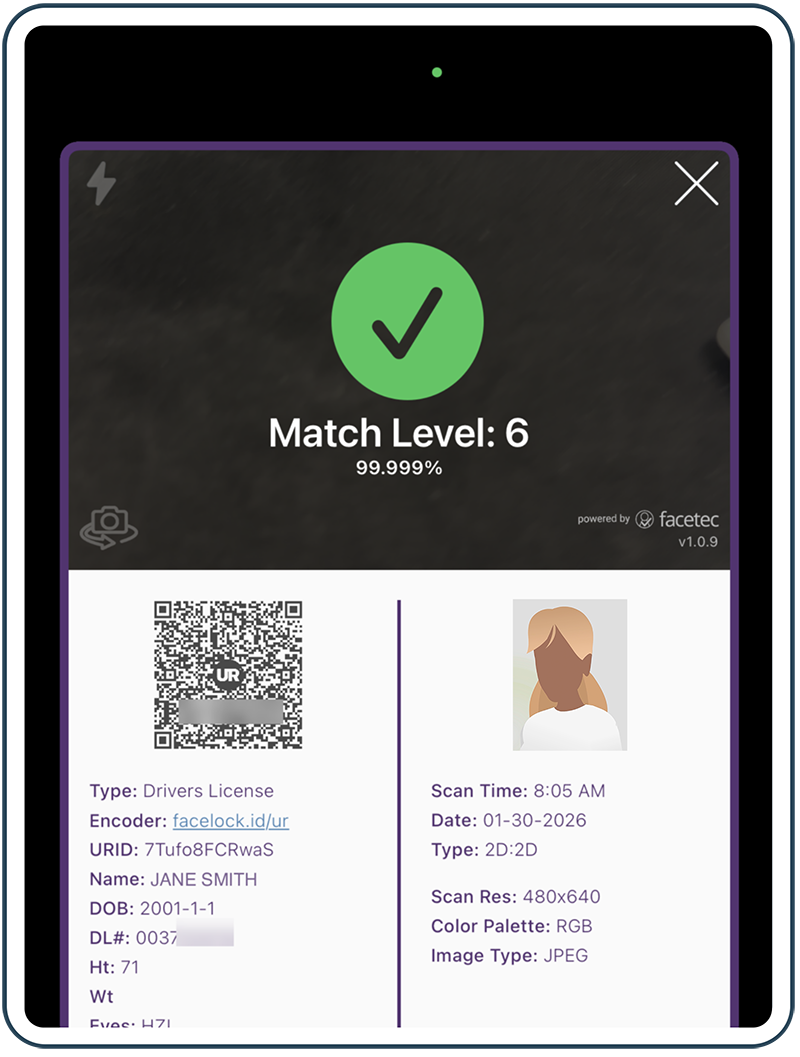
Trust
Receive instant verification result - no internet required
Trusted by Leading Organizations
FaceLock serves government agencies, educational institutions, healthcare organizations, and more
See How FaceLock Solves This
Learn how biometric binding eliminates the analog gap and prevents credential fraud